
SCADA RISK ANALYSIS
POTENTIAL EXCEPTIONS AND PROBLEMS
Cyber Security is important to the safety and reliable operations of SCADA networks. There are different types of cyber security issues we often see in SCADA networks that can impact system operations in spite of security measures that are put in place, such as firewalls. Most cybersecurity issues fall into the following categories: Network Design, Physical Access, Environmental Impacts, Endpoint Configuration, and Data Transmission and Storage.
Network Design
Vulnerabilities can exist within a system that has interconnected networks where the design has utilized poor network segmentation. The misconfiguration or nonuse of border protection devices such as firewalls to separate networks can allow unwanted traffic to propagate between connected networks. Exhibit 3.1 shows malicious traffic flowing from a device across networks that do not have border protection.
Physical Access
Physical damage, unauthorized access to equipment, and the introduction of unauthorized devices are examples of vulnerabilities that exist for inadequate physical security. Failing to monitor who has access and not placing equipment in secured areas can lead to damage. Exhibit 3.1 illustrates the potential damage caused by a bad actor having unauthorized physical access to the network.
Exhibit 3.1 - Network Design/Physical Access Attack Example
Environmental Impacts
The environment the SCADA system is installed in creates vulnerabilities that must be addressed. SCADA systems are vulnerable to damage from environmental factors such as natural disasters. Damage can also occur from things such as fire or water damage from leaking piping systems.
Endpoint Configuration
Security vulnerabilities exists within network endpoints such as workstations, servers, network hardware, and controllers resulting from improperly configured or missing security controls. Workstations and servers running legacy OS cannot be configured with the latest security patches. Poor patch management, missing or misconfigured security controls, and malware/virus protection not used or out of date are vulnerabilities that can lead to system compromises. This also applies to network hardware such as firewalls, switches and routers. Exhibit 3.2 illustrates the potential damage caused by a bad actor attacking a misconfigured switch and causing a network storm.
Data Transmission and Storage
Vulnerabilities to data confidentiality, integrity, and availabilities exists within SCADA networks. Security controls and configurations that do not address network attacks such as snooping, modification, or denial of service will have negative effects on data being transmitted or being stored. Exhibit 3.2 illustrates the potential damage caused by a bad actor performing a denial of service attack.
Exhibit 3.2 - Endpoint Configuration/Data Transmission and Storage Attack Example
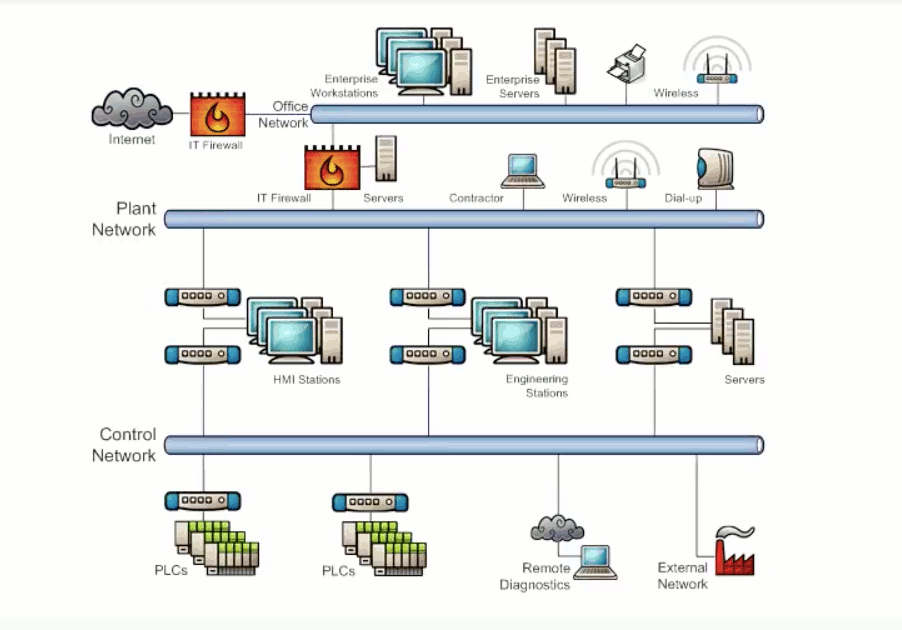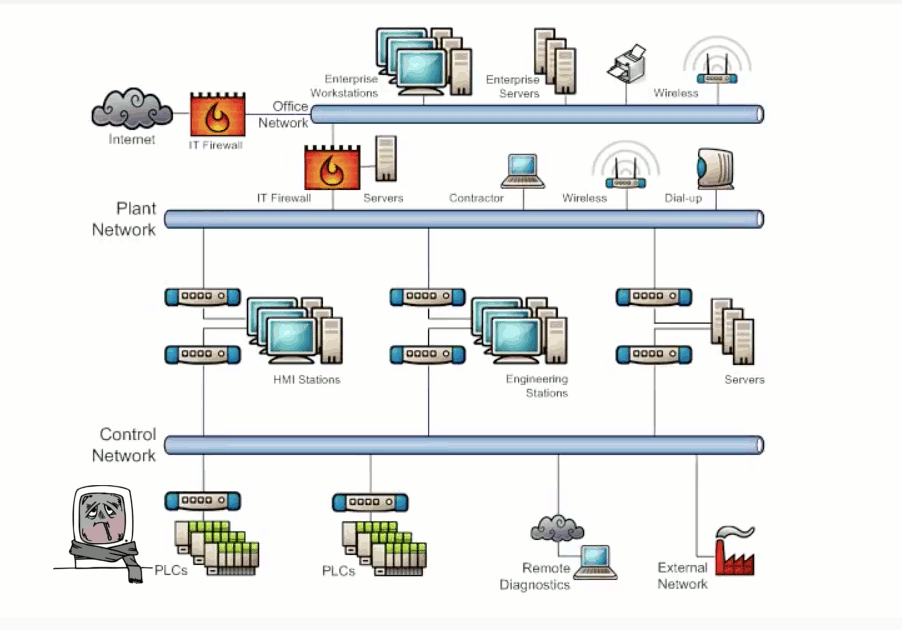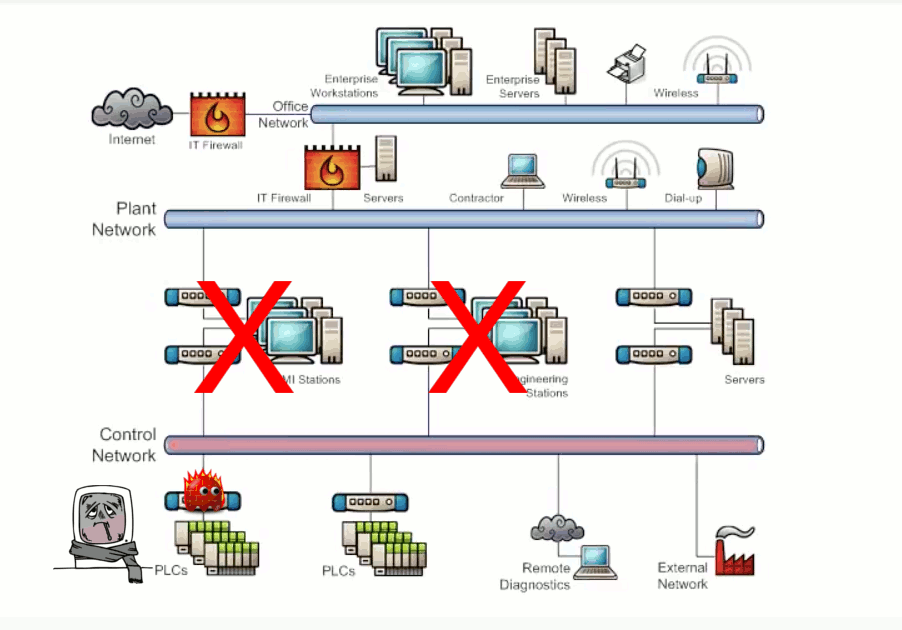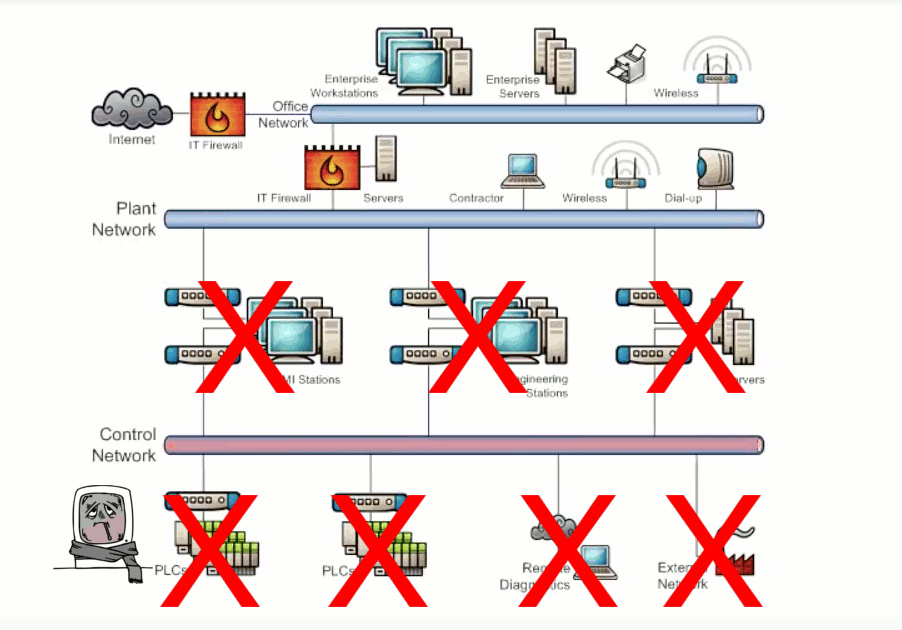
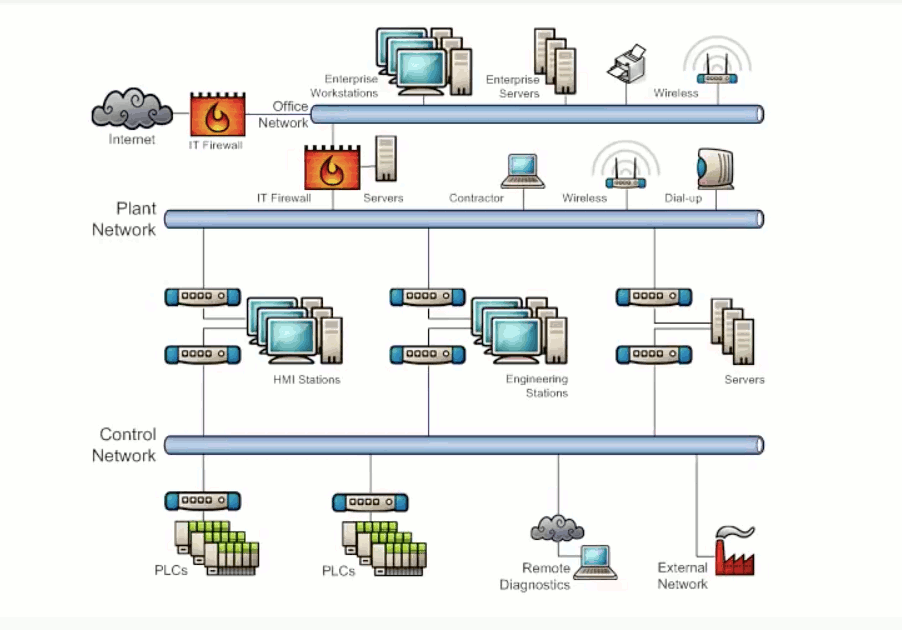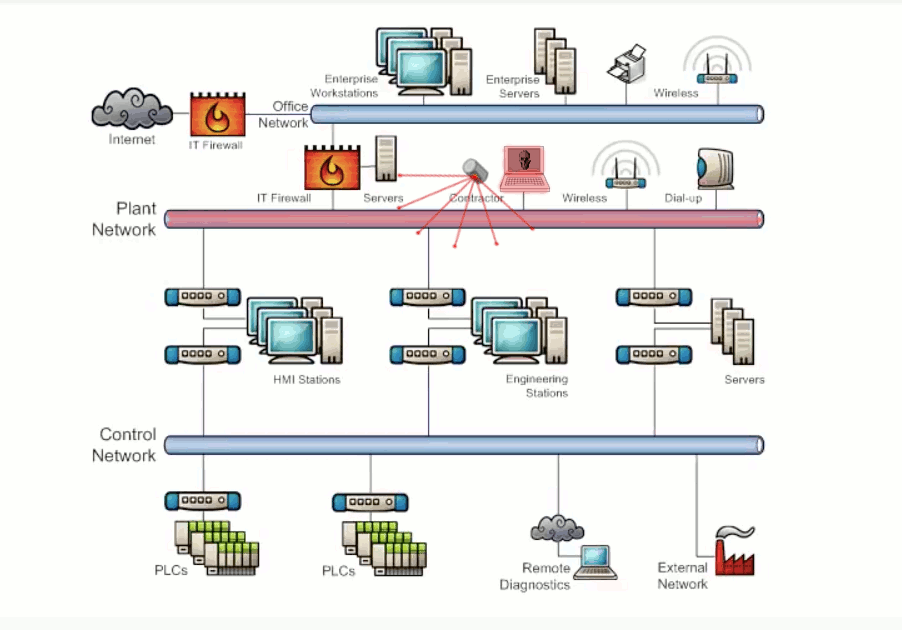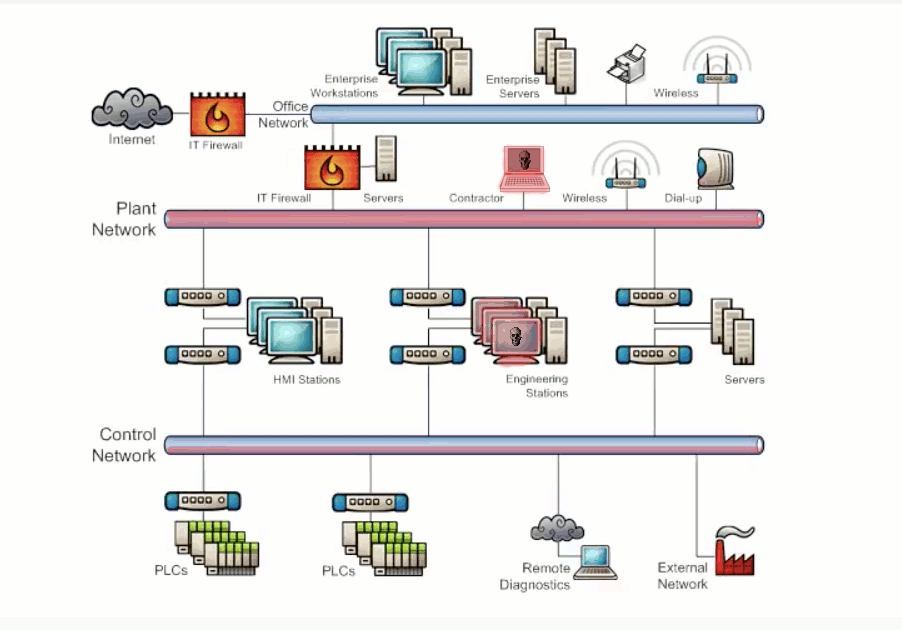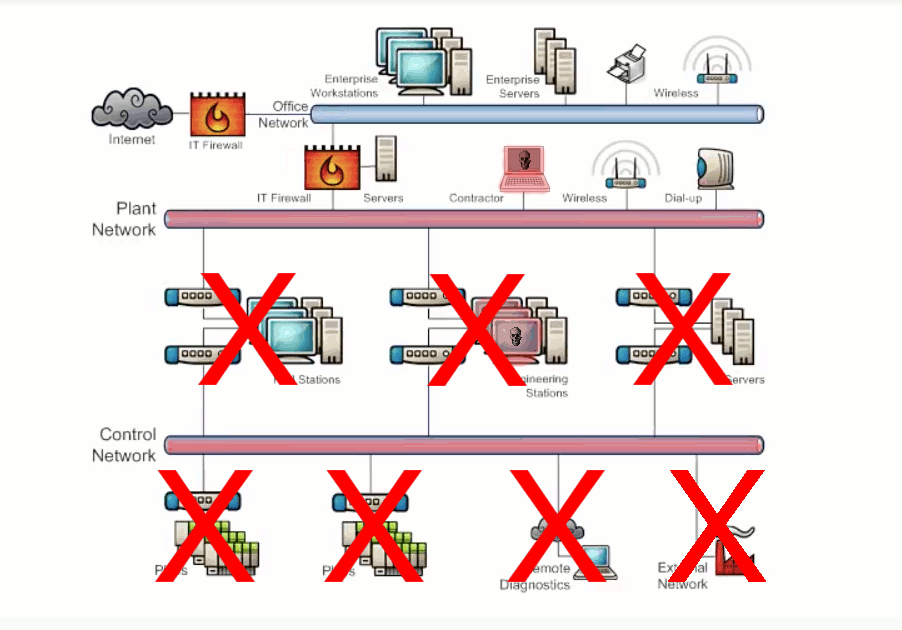
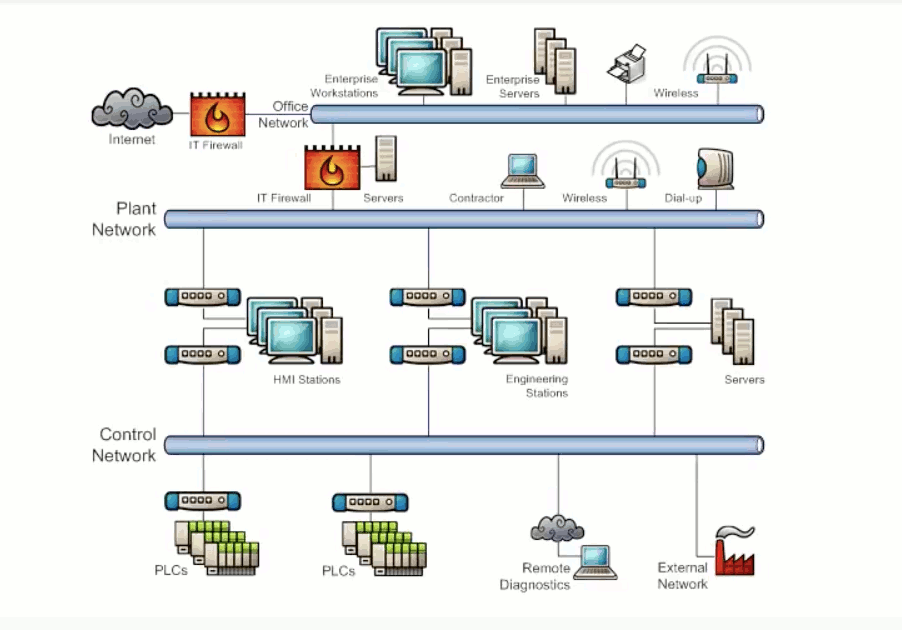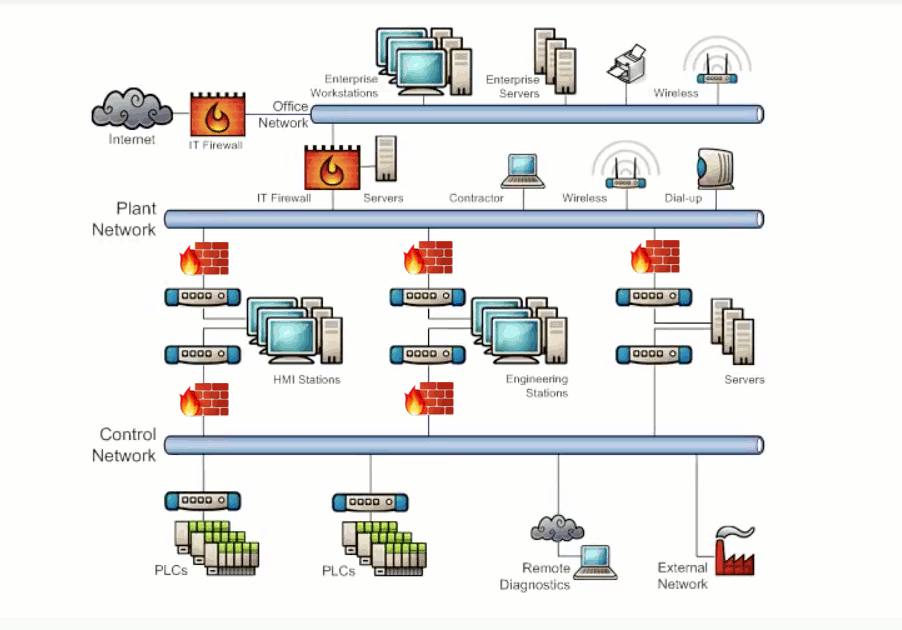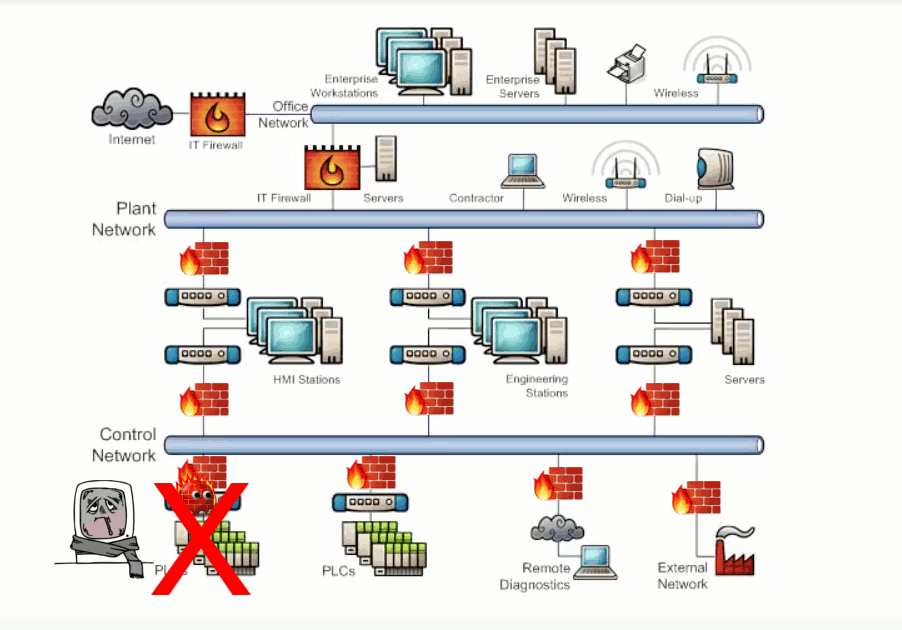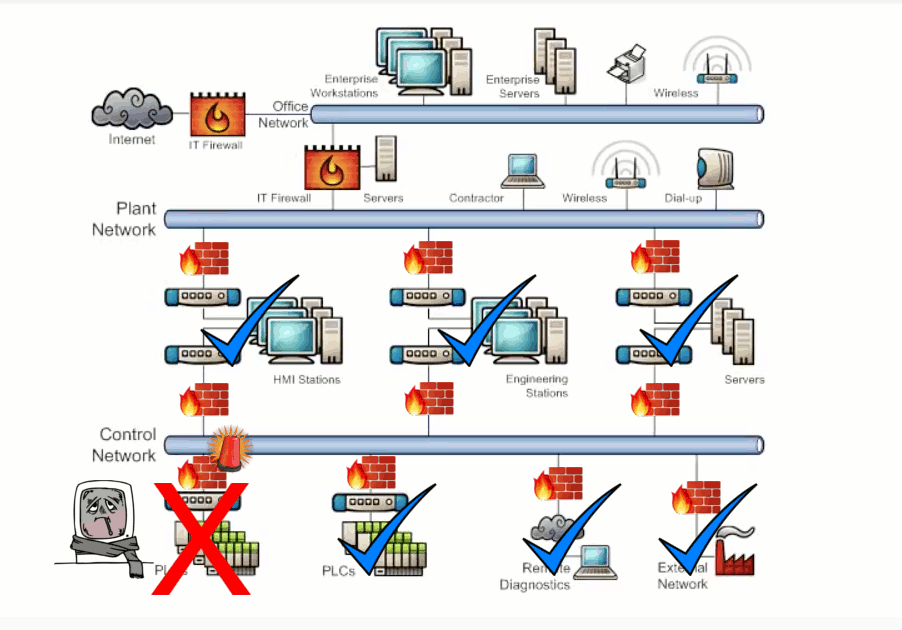
Exhibit 3.3 shows a simplified diagram of a typical SCADA system. The PLCs and sensors are connected to a control network which is isolated from the main system network by dual homed PCs. The system network in turn is isolated from the enterprise network by a firewall. Finally, the enterprise network is isolated from the internet by another firewall. If properly configured, the firewall on the system network will be able to stop cyber security threats that originated from the internet or the enterprise network.
Exhibit 3.3 - Typical SCADA Diagram - Simplified

APPROPRIATE CORRECTIVE MEASURES
Defense in depth is an effective strategy to combat cyber security threats. This strategy creates multiple layers of defense between the threat source and the critical assets By using the ISA 99 standard - zones and conduits.
-
ISA 99 standard – zones and conduits: security zone:grouping of logical or physical assets that share common security requirements (ANSI/ISA-99.01.01-2007-3.2.116); a zone has a clearly defined border (either logical or physical) which is the boundary between included and excluded elements.
Zones are defined by the groups of critical equipment. The conduits of communication exist between these zones and once we know where all those conduits are we can then install a firewall in each conduit and configure it to allow only the minimum network traffic that is required for correct system operation and block all unnecessary traffic to ensure that when a problem happens in one area of the network it won't be able to spread. Additionally this will generate alarm messages when traffic is blocked so we will know when and where a problem occurs in the network and be able to respond quickly to resolve it. Exhibit 3.4 shows how defense in depth is used to protect Network Design and Physical Access. Exhibit 3.5 shows how defense in depth is used to protect Endpoint Configuration and Data Transmission and Storage.
Exhibit 3.4 - Defense in depth strategy for Network Design and Physical Access
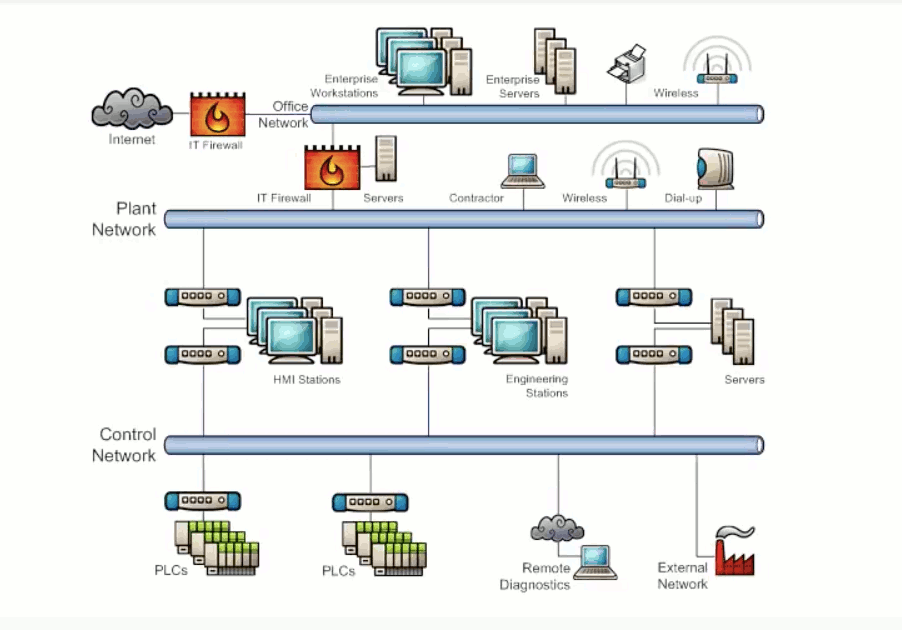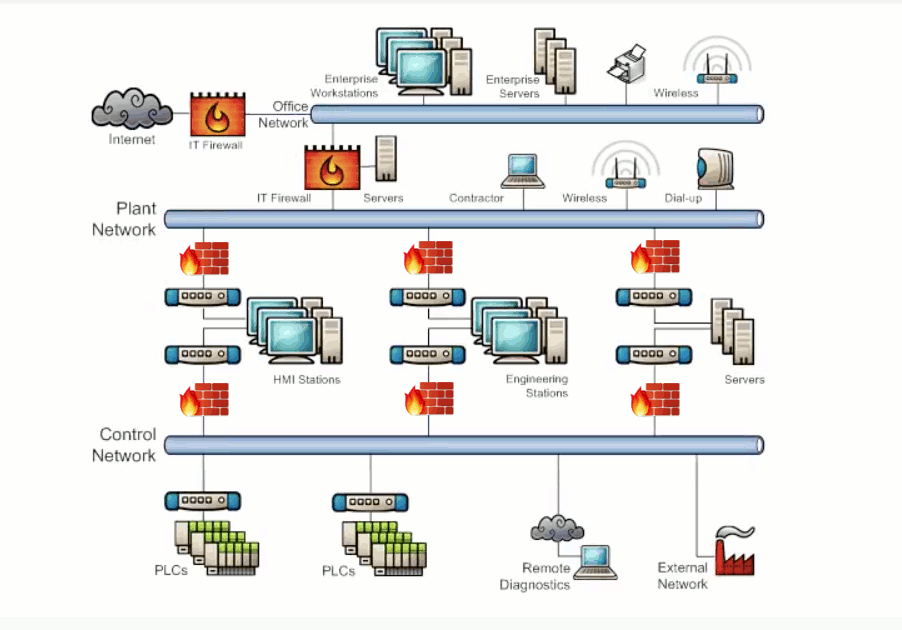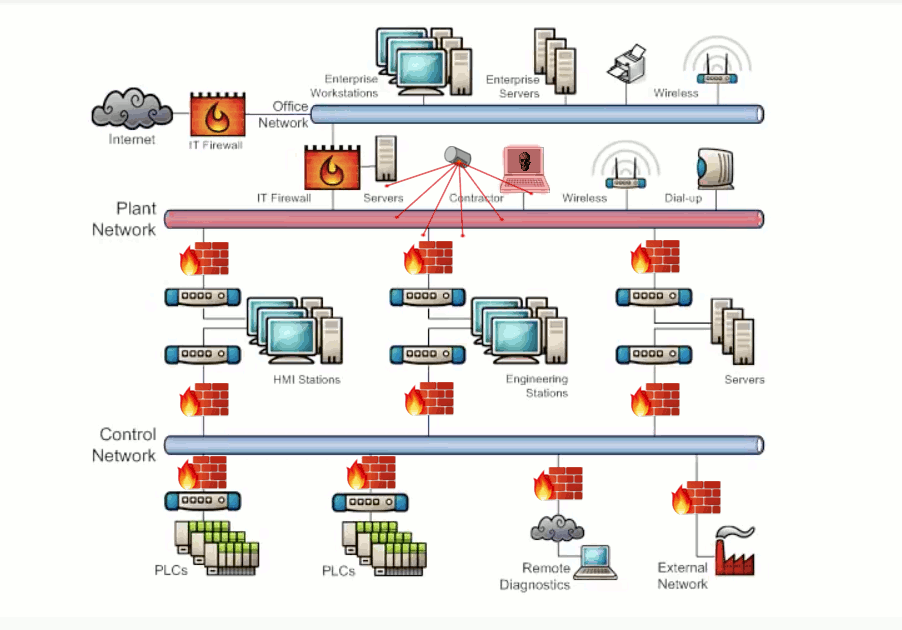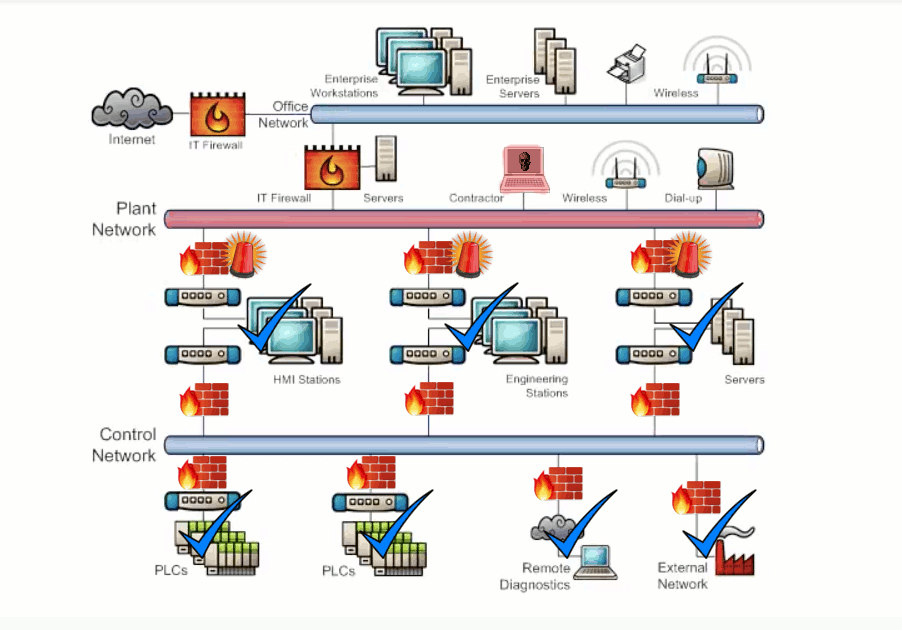
Exhibit 3.5 - Defense in depth - Endpoint Configuration and Data Transmission and Storage
The traditional perimeter model of defense is not effective against accidents, malware, or device failures that occur inside the system network. Defense in depth is a strategy that works, and when it is used properly it will keep the system up and running when problems do occur. It will also help to quickly locate the source of the problem and resolve it. By combining the right tools with the best practices outlined in the ISA 99 standard, implementing a defense in depth strategy quickly will help to reduce the downtime of the system and create enhanced productivity.